Do you know if your network is vulnerable to hackers? Do you want to prevent data breaches and cyber-attacks that could damage your reputation and cost you money? If so, you need to test your network security regularly with our network penetration testing service.
Penetration testing is a simulated hacking attempt that reveals the weaknesses and risks in your network. As part of our service, we will try to break into your network using the same methods and tools as real hackers. Then we will report our findings and recommendations to help you fix the issues and improve your security.
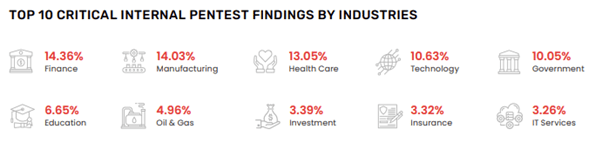
Based on network penetration tests completed on over 2000 organisation since 2019, these are the top 10 Critical internal pentest findings on the most recent 1500 security tests performed globally
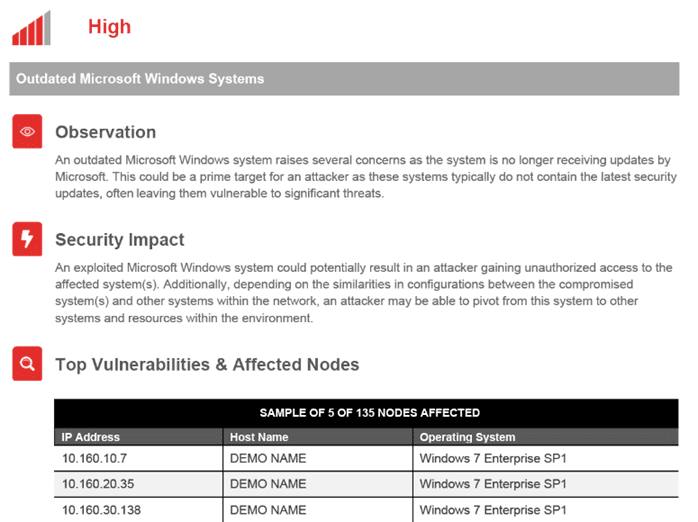
These are the common vulnerabilities that hackers exploit to compromise your network and access your data.
Network Penetration testing is a security assessment that mimics a real hacking attack on your network. It aims to find and exploit the vulnerabilities and gaps in your network security. It’s like a health check for your network that shows you how well you are protected from cyber threats.
A vulnerability assessment is a scan that detects the potential vulnerabilities in your network. It tells you what problems you have, but not how serious they are or how to fix them. A penetration test goes a step further and tries to exploit the vulnerabilities to see what damage they can cause. It tells you how severe the problems are and how to fix them.
Our penetration testing service is designed to help you improve your network security and comply with industry standards and regulations. We offer:
The report is the final deliverable of the penetration test. It contains all the information you need to understand and improve your network security. The report includes:
Executive summary: A high-level overview of the objectives, scope, methodology, results, and conclusions of the penetration test.
Technical details: A detailed description of each finding, including the vulnerability, the risk, the exploit, the impact, and the recommendation.
Evidence: A collection of screenshots, logs, and other artifacts that support the findings and demonstrate the exploitation.
Appendix: A list of references, tools, and resources used during the penetration test.